By default WordPress allows PHP files in the uploads directory to be executed.
Under normal circumstances this shouldn’t be a problem – but all it takes is for a vulnerable plugin to allow a PHP file to be uploaded. Or perhaps the plugin allows a text file called script.txt to be uploaded and then allows it to be renamed to script.php
For a hacker, this is the holy grail of exploits – they get full access to the website and the server.
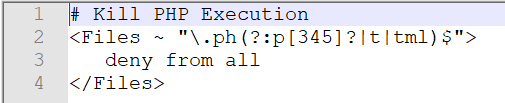
It can however be easily avoided by creating an .htaccess file in your uploads directory and adding the code shown below. This will prevent PHP files in the uploads directory from being executed.
Note: this is for Apache servers only. If it doesn’t work it’s likely you do not have an Apache server.
# Kill PHP Execution <Files ~ "\.ph(?:p[345]?|t|tml)$"> deny from all </Files>