A “honeypot” is a security method which can be used to catch wrong-doers and learn more about their activities.
For each login attempt the honeypot recorded:
- the IP address
- the username
- the password
- the date and time.
This was done using an up-to-date WordPress install (WordPress 5.0.3) and the WP Login Attempt Log plugin.
To limit this to only the most persistent wrong doers – I used Limit Login Attempts Reloaded to automatically block the IP address after one attempt and had CloudFlare set to “I’m under attack mode”.
Here’s what I learned from the data.
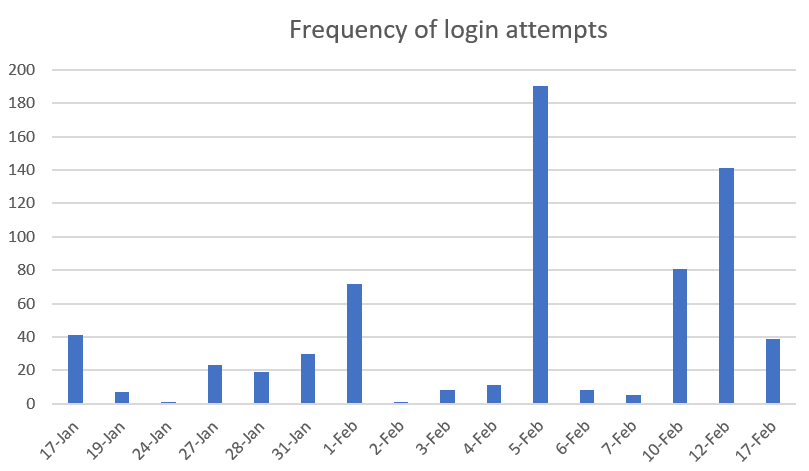
Frequency
During this month I recorded 676 login attempts – that’s an average of 42 a day.
Some days saw only a handful of attempts and others were hammered – the biggest day was 190 unique attempts.
This irregular frequency leads me to think that it’s not just bots – but also real humans manually trying.
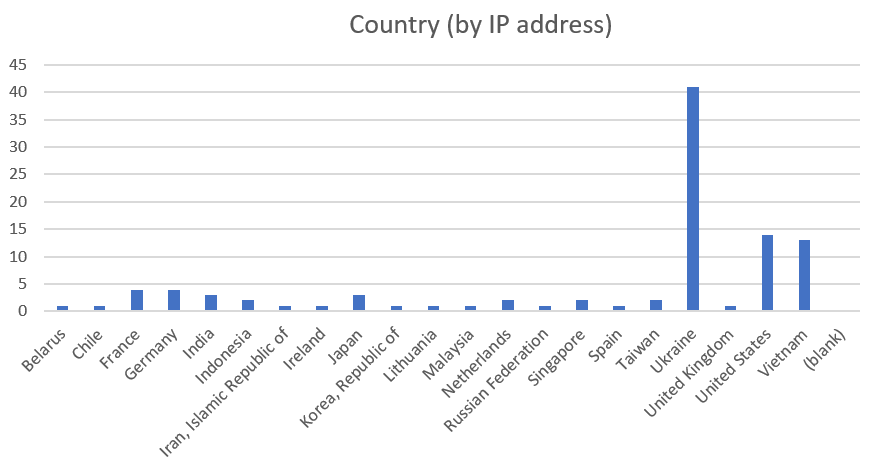
Country
With VPS and cloud computing being so prevalent – telling the country by the IP address needs to be taken with a grain of salt.
This might just come down to cheap cloud hosting or IP address allocations.
Matching the IP address with the country designation showed Ukraine was the most frequent country.
The top five were:
| Country | Count |
|---|---|
| Ukraine | 41 |
| United States | 14 |
| Vietnam | 13 |
| France | 4 |
| Germany | 4 |
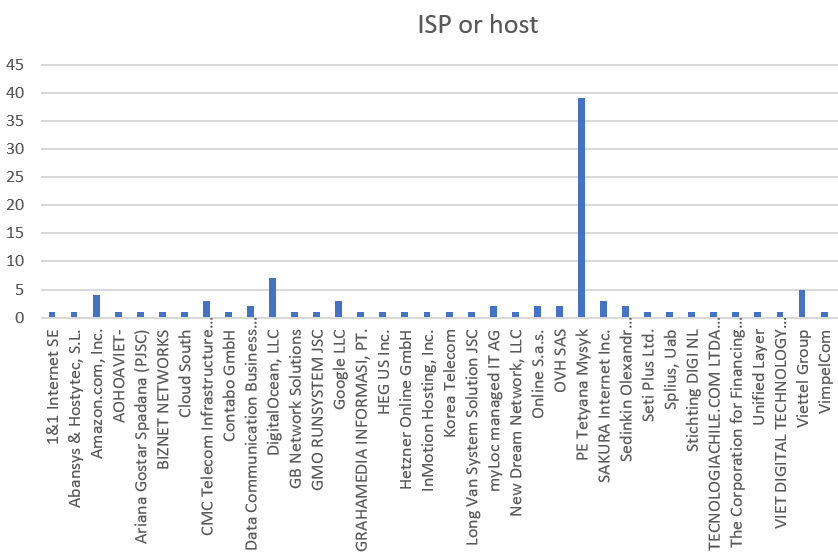
ISP or host
Again, using the IP address we can determine the ISP or host – being who has ownership of the IP address.
PE Tetyana Mysyk was the most frequent – which was associated with the Ukraine attempts.
But unsurprisingly, Digital Ocean and Amazon – which are popular cloud VPS hosts – also made a show.
The top five were:
| ISP or host | Count |
| PE Tetyana Mysyk | 39 |
| DigitalOcean, LLC | 7 |
| Viettel Group | 5 |
| Amazon.com, Inc. | 4 |
| CMC Telecom Infrastructure Company | 3 |
Login method
WP Login was significantly the login method attempted.
With the data I have I can only assume this was by sending a post request to wp-login.php – rather than visiting the page using a browser.
| Login method | Percent |
|---|---|
| WP Login | 94.24% |
| XMLRPC | 5.76% |
Usernames attempted
Majority of attempts used the author username, but there was also a lot of generic usernames used.
The top five were:
| Username | Count |
|---|---|
| hpotuser | 184 |
| [login] | 161 |
| admin | 117 |
| wpdevguides | 40 |
| test | 36 |
* note:
- hpotuser – was the author account used to create posts/pages
- wpdevguides – was the top level domain for the WordPress install
The full list was:
- hpotuser
- [login]
- admin
- wpdevguides
- test
- testuser
- 123
- demo
- teste
- editor
- dexter
- 123456
- testing
- 111
- 0x1999
- admin2
- asd
- guest
- jake
- jsjobs_employer
- patricia
- prova
- prueba
- roottn
- test123
- user1
- xrumertest
- 1234
- 123123
- [login][login]2017
- [login][login]2018
- admin1
- AnonymousFox
- asdasd
- badmin
- kenneth
- magico
- manager
- phukotler
- schatzi
- student
- test1
- user
- useradmww2
- wpupdateuser
- 12345678
- 123456789
- [login]12345678
- diysite
- garak
- indoxploit
- local
- localdev
- preview
- qwerty
- testtest
- wpmu
Passwords used
The passwords used were surprisingly simple. If someone has ownership of a website and uses passwords this simple … well they’re just asking to loose the website.
The top five were:
| Password | Coun |
|---|---|
| 123456 | 36 |
| admin | 20 |
| password | 20 |
| 123456789 | 14 |
| 123 | 11 |
* note:
- hpotuser – was the author account used to create posts/pages
- wpdevguides – was the top level domain for the WordPress install
The full list was:
- 123456
- admin
- password
- 123456789
- 123
- test
- test123
- [login]
- test1234
- 1234
- admin123
- demo
- wpdevguides123
- Admin@123
- 1234567
- changeme
- F*uckYou
- wpdevguides
- password1
- 12345
- [login]@123
- Admin123!
- wpdevguides2016
- manager
- pass
- test1
- 1
- 123123
- 12345678
- [login]!@#
- hpotuser123
- guest
- wpdevguides2018
- letmein
- passw0rd123
- password123
- root
- secret
- sysadm
- teste
- testing
- 111
- 987654321
- [login]!
- [LOGIN]!!!
- [login]@1
- [login]@2012
- [login]@2018
- [login]@2019
- [login]@321
- [login]1
- [Login]12345
- [login]2016
- [login]2017
- [login]2018
- [login]654321
- 0x1999
- abcd1234
- admin!!!
- admin@123!
- admin2
- adminpass
- adminpw
- adminpwd
- asd
- dayat12345
- dragon
- editor
- fuck
- wpdevguides@2017
- wpdevguides2014
- wpdevguides2017
- K98pWjiSq12
- letmein1
- master
- monkey
- P@ssw0rd
- p@ssword
- p@ssword1
- p@ssword123
- pa55w0rd
- passw0rd
- passw0rd1
- passwd
- patricia
- prova
- prueba
- superman
- system
- testtest
- testuser
- user1
- vodka
- welcome
- 111111
- 112233
- 1234567890
- @[login]
- @[login]@
- [login]@)!
- [Login]@)!(
- [login]@1234
- [login]@2014
- [login]@2015
- [login]@2016
- [Login][login]
- [Login]001
- [login]01
- [Login]111
- [Login]12
- [login]123
- [login]123!
- [Login]123@
- [login]2012
- [login]2015
- [login]2019
- [login]321
- [Login]444
- [login]777
- [Login]888
- [login]pass
- abc123
- admin@!
- admin@#$
- admin@2020
- admin@33
- admin@333
- admin@345
- admin1
- admin1234
- admin12345
- adminadmin
- hpotuser
- AnonymousFox
- asdasd
- baseball
- Cvvfaqf1vsd5
- demo123
- editor123
- F*uckYou123
- guest1234
- hello
- iloveyou
- indoxploit
- wpdevguides.com
- wpdevguides@#$
- wpdevguides@33
- wpdevguides@345
- wpdevguides2015
- kenneth
- logitech89
- qwerty
- qwerty123
- ricsky789..
- sa
- student
- xmagico
- 1111
- 654321
- 12341234
- [login]@)!*
- [Login]@)!^
- [login]@001
- [login]@01
- [Login]@2013
- [login]@2017
- [login]@2020
- [login][login]2018@01
- [login]1234
- [login]123456
- [login]2013
- [login]2014
- [Login]2020
- [login]333
- [login]666
- [login]999
- 123qwe
- 1q2w3e4r
- 1qaz2wsx
- a
- adcde12345
- admin@!!
- admin@2017
- admin@2018
- admin@2211
- admin@2222
- admin@3
- admin@321
- admin@40
- admin@432
- admin@44
- admin@444
- admin@456
- admin@5
- [email protected]
- admin01
- admin123@
- admin2018
- hpotuser!
- hpotuser@123
- hpotuser01
- hpotuser10
- hpotuser11
- hpotuser12
- hpotuser1234
- hpotuser123456
- hpotuser2016
- hpotuser2017
- hpotuserhpotuser
- ashley
- baglisse
- football
- iloveyou1
- wpdevguides!
- wpdevguides@!
- wpdevguides@!!
- wpdevguides@123
- wpdevguides@2019
- wpdevguides@2020
- wpdevguides@2222
- wpdevguides@3
- wpdevguides@333
- wpdevguides@4
- wpdevguides@40
- wpdevguides@432
- wpdevguides@44
- wpdevguides@444
- wpdevguides@456
- wpdevguides1
- wpdevguides10
- wpdevguides11
- jesus
- local
- michelle
- preview
- shadow
- sunshine
- temporal
- test12
- test123456
- trustno1
- xxx
What did I learn?
The honeypot worked – I caught a decent sample of brute force login attempts.
I’ve learned:
- the attacks are happening all the time – seemingly from several sources – don’t ever let your guard down and always keep a backup
- never include your domain name in the username or password
- the author username is a hot target – never give it full administrator access